Despite the crypto industry’s ongoing cybersecurity efforts, protocols are engaged in an endless war with cryptocurrency hackers, who continue to attack the weakest link in crypto protocols, which is often a human behavioral element.
The industry is engaged in unfair warfare with bad actors, who only need a single point of vulnerability to exploit a protocol, according to Ronghui Gu, professor of computer science at Columbia University and the co-founder of blockchain security platform CertiK.
“As long as there’s a weak point or some vulnerabilities out there, sooner or later they will be discovered by these attackers,” said Gu, speaking during Cointelegraph’s Chain Reaction daily live X spaces show, adding:
“So it's an endless war.”
“But I’m afraid that next year’s [hacks] will still be at a billion-dollar level,” said Gu, adding that both cybersecurity efforts and cybercriminals are becoming stronger. Still, attackers only need to find a single bug in the millions of lines of code audited daily by CertiK
Losses to crypto hacks and exploits spiked to $2.47 billion in the first half of 2025, despite declining hacks in the second quarter. Over $800 million was lost across 144 incidents in Q2, a 52% decrease in value lost compared to the previous quarter, with 59 fewer hacking incidents, CertiK said in a report on Tuesday.
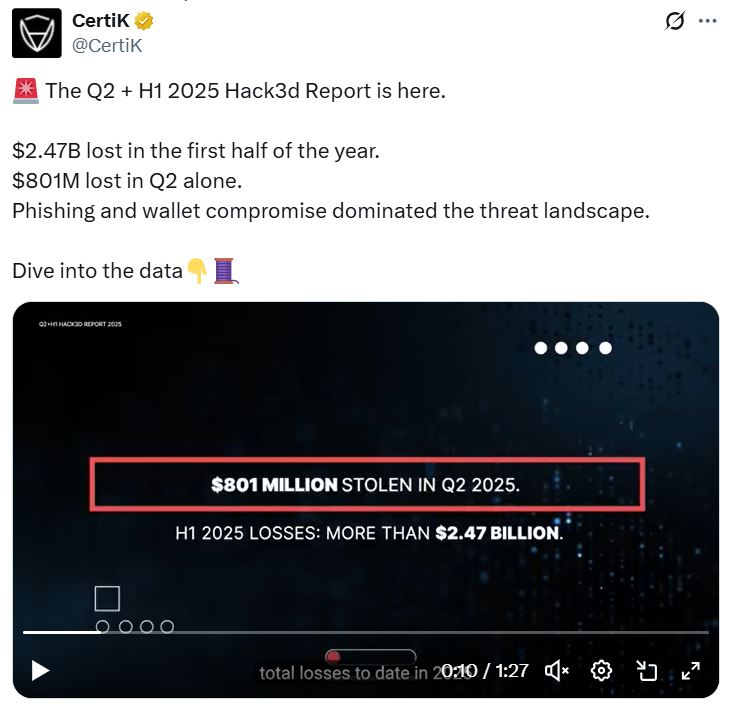
The first half of 2025 has seen more than $2.47 billion in losses due to hacks, scams and exploits, representing a nearly 3% increase over the $2.4 billion stolen in all of 2024.
The lion’s share of the lost value was attributed to a single incident, a $1.4 billion Bybit hack on Feb. 21, marking the largest cyberexploit in crypto history.
Blockchain cybersecurity improvements will force hackers to target human behaviour
The industry’s ever-evolving cybersecurity measures are forcing hackers to look for new vulnerabilities to exploit, including loopholes in human psychology, according to CertiK’s Gu, who explained:
“Let's say that your protocol or layer 1 blockchain becomes more secure. Then they may target human beings behind it. The people who have the private key and so on.”
